Healthcare organizations are in a global state of emergency — not only due to the pandemic, but because hackers are targeting their cyber security shortcomings.
Numerous studies show that the healthcare industry is the biggest target for hackers. Organizations that fall victim to a cyberattack could face hefty fines and significant reputation damage. Not only that, but your patient data could also be compromised, putting their information in the hands of a malicious hacker.
I recently partnered with my colleague Steve Rutkovitz from Choice Cybersecurity to identify the current threats healthcare organizations are facing and how to minimize the risk of an attack in the future. Let’s jump in and explore the five-step process for how to take your HIPAA security to the next level and achieve true cyber health.
1. Perform a Risk Assessment
When performing a risk assessment, your first step should be to build a baseline for your organization. The baseline takes a deep dive into your organization’s risk and compliance, which uncovers the gaps in your cyber security plan and exposes your current vulnerabilities.
Once you have a snapshot of the current threats you are facing, you can analyze the layers of defense, identify your sensitive data and gain a full understanding of your missing controls and policies. At the end of the assessment, our team provides an executive summary that targets problem areas in your network as well as recommendations to help you improve your organization’s risk and compliance.
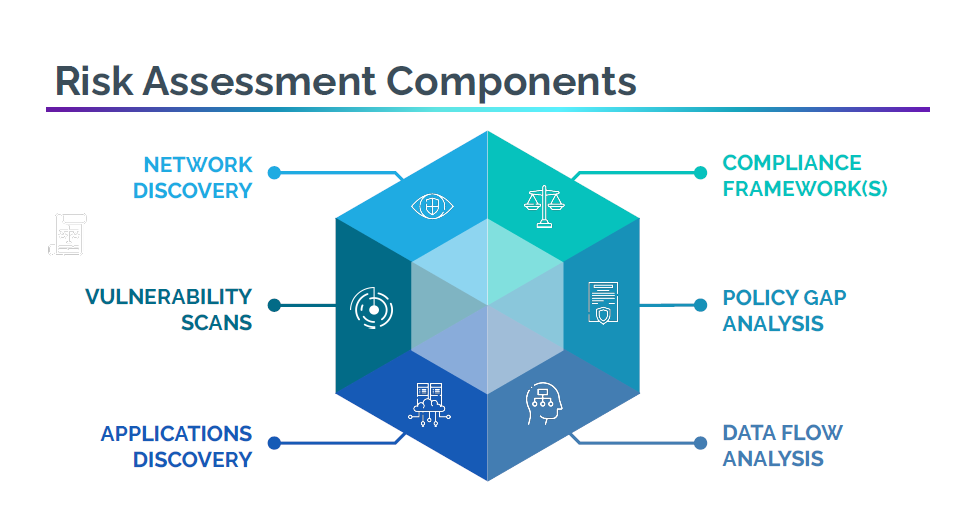
As you begin to evaluate your vulnerabilities, you’ll be able to assess whether you meet the compliance framework for HIPAA, NIST and CRISP and discover what’s holding you back from meeting compliance requirements.
2. Build Your Remediation Plan
Once you pinpoint the gaps in your organization’s cyber security plan, you can organize your remediation plan.
Your first step is to develop a Plan of Action & Milestones (POAM) where you’ll break down the stack of security measures needed to protect your organization from a ransomware attack or cyber hack.
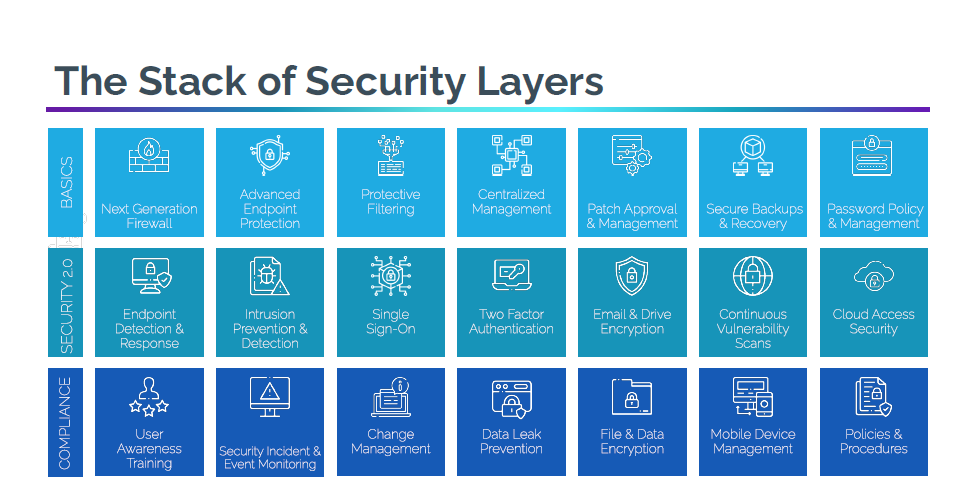
When reviewing your security layers, you’ll prepare your System Security Plan (SSP), the goal of which is to preserve your healthcare organization’s information. When we help organizations with system security plans, our job is to scan and assess the network infrastructure for risk and compliance issues, then provide a full set of tools to reach and maintain compliance.
This advanced analysis is essential for documenting compliance concerns and cyber security vulnerabilities. The most important factor to know during this assessment is that your information will NEVER be shared.
3. Execute Your Plan
Now that you’ve laid out the baseline of your security plan, it’s time to develop your execution plan.
First, you’ll execute your POAM and SSP. This will lead you to develop your policies and procedures, ensuring you’re compliant with HIPAA, NIST and CRISP.
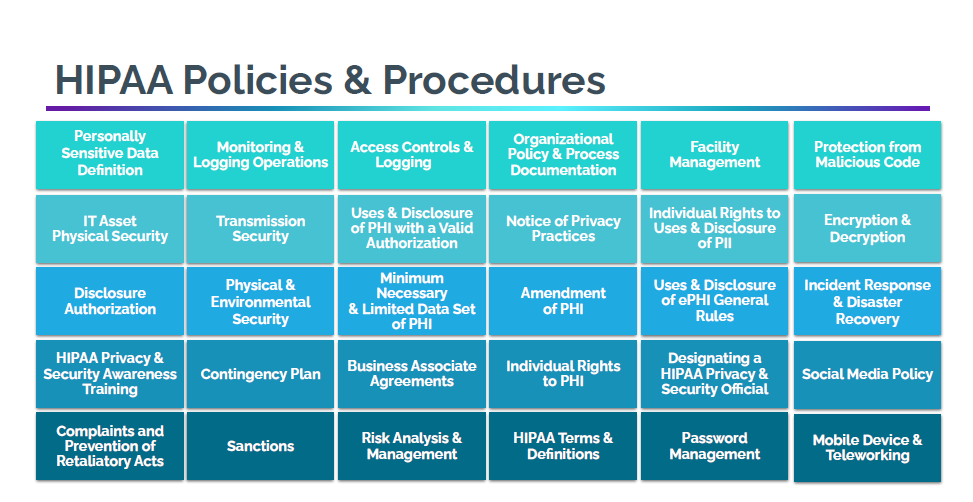
As you continue on your compliance journey, you will be able to implement your risk and compliance tools, safeguarding your healthcare organization from those malicious hackers.
Antivirus, dark web monitoring and other software can be cumbersome to setup on your own, which is why we’ll help you find the right software for your healthcare organization, get it working and make sure it meets your price point. Your organization may even qualify for the Maryland Cybersecurity 50% Tax Credit.
4. Organize and Document Your Plan
Now that your plan is in place, it’s time to get organized! It is critical to certify that the vendors you work with meet compliance requirements and are aware of your policies and procedures. By documenting your policy, you’ll be able to distribute your plan to vendors during the onboarding process, preserving your security and compliance measures.
After you document your plan and distribute it accordingly, you’ll be able to establish Standard Operating Procedures (SOPs). As you establish your workflow and provide training for your staff on your new policies and procedures, your team will understand how to protect patient data, how your organization meets compliance standards needed to operate and understand the IT capabilities needed to secure your organization.
5. Prepare for Ongoing Maintenance
As you wrap up your compliance journey, you are now audit-ready. Once you complete your audit, put a compliance management strategy in place to ensure your newly developed plan is maintained. One way to do this is to complete an annual risk assessment to make sure your organization stays up to date with current security measures, protecting your healthcare organization from a ransomware attack.
Need Help?
The risks of not having a solid cyber security plan, policies and certifications in place are enormous. A cyberattack puts patient data and your reputation at risk and could bring your healthcare organization to a screeching halt.
If you have questions on how to get started with your cyber security plan, connect with us online or give us a call at 410.685.5512.
P.S. You can check out our on-demand webinar, Healthcare In Crisis: How to Take Your HIPAA Security to the Next Level, here.


