Public Wi-Fi seems almost ubiquitous these days. Lots of locations and establishments like to offer it as a perk for you to take advantage of. However, not every organization responsible for these public networks properly secures them.
This gives cyber attackers the opportunity to entice people to connect to a network impersonating an organization or to unsecured public networks where they can launch attacks.
Fortunately, you can protect your devices and information from these sorts of threats. Here are some ways to increase your safety and thwart would-be attackers.
Use Your Mobile Hotspot
If you have a mobile hotspot on your device, use that instead of the free Wi-Fi. This way, you know you’re connecting to a trusted device and network, and no one else will be connecting with you. (Be sure to use a strong password for your hotspot connection login!)
Use a VPN
A Virtual Private Network (VPN) will protect your internet traffic from being seen by those on the same network. This will hinder many types of attacks.
When we talk about using a VPN, there are three different scenarios we might be referring to:
VPN Services
In commercials and ads, you’ll see companies selling their VPN services. With VPN services, you send all your encrypted traffic to the VPN provider, and then it exits onto the Internet. This prevents data gathering and attacks from bad actors that are on the same network. It can also circumvent geo-restrictions in place for services.
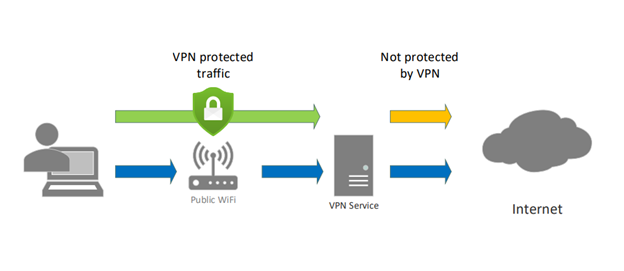
VPN services
Corporate/Business VPN “Split Tunnel”
The purpose of a corporate VPN is to create a secure connection to allow access to business resources.
Traffic for the corporate network is encrypted and sent to the VPN server. All other traffic is sent directly out to the Internet. A business VPN “split tunnel” doesn’t protect you when on public Wi-Fi for any services not located on the corporate network.
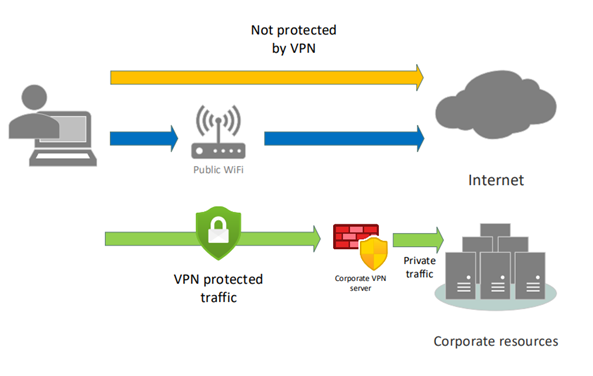
Corporate/business VPN “split tunnel”
Corporate/Business VPN “Full Tunnel”
The corporate VPN “full tunnel” is like the “split tunnel” scenario, but in this case, all traffic is sent to the VPN server. This can be the strongest and safest option for protection as corporate firewalls will often have advanced security features to better protect the traffic.
Ask your IT department which type of VPN you have. If it’s not a full tunnel, use a VPN service or hotspot.
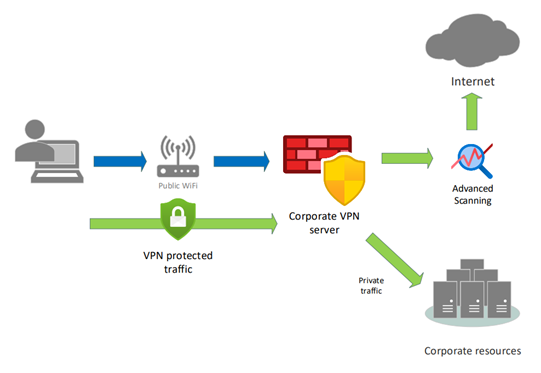
Corporate/business VPN “full tunnel”
What If You Don’t Have a VPN or Hotspot, But Need Information?
If you’re saying, “That’s all great for those who have a hotspot or VPN, but I don’t,” then there are some limited alternatives you can do on your own to try to stay safe.
- Only gather information from reputable sites
- Do not download anything
- Do not log on to any website or service
These best practices won’t guarantee your protection but will reduce the opportunity for a cyberattack to take place.
Need Help?
Our Technology Solutions Group includes a team of cyber security experts. We’re happy to meet with you for a cyber security risk assessment of your organization’s IT infrastructure. Or, you can contact us online or call 410.685.5512 with any questions.


