Reports show that government contractors are one of the largest targets for hackers. Businesses that fall victim to a cyber attack could face loss of contracts, reduced funding, significant reputable damage or substantial recovery fees.
Most government contracts require Federal Information Security Management Act (FISMA) and National Institute of Standards and Technology (NIST) compliance to prevent security and cyber breaches.
Now, the Department of Defense (DoD) is taking it a step further and will require CMMC compliance starting October 1.
So, what exactly is CMMC and how do you take your certification across the finish line to obtain true compliance? Let’s break it down for you."
What is CMMC, who's required to have it and what is the difference between CMMC and NIST 800-171?
CMMC is short for Cybersecurity Maturity Model Certification. This level of compliance will be a requirement for every contractor and subcontractor looking to obtain a government contract. The key difference between NIST 800-171 and CMMC is that NIST is a self-assessment. Though it is recommended that you partake in a self-assessment on a yearly basis, the certification will be valid for three years and will ensure you meet the requirements for compliance.
Now that it's a known fact that you will need to obtain the CMMC certification, how do you get there?
Steve Rutkovitz, the co-founder and CEO of Choice Cybersecurity outlines the first step as “Assess, address and maintain.”
He notes, “If you assess and understand your level of risk, you are able to address any issues, and maintain the solutions you put in place.”
When you begin your risk assessment, you are provided with a compliance framework. This is where you identify what is already compliant and do your gap analysis to find missing requirements that are not in place.
Once you have reviewed your framework, it is time to run a vulnerability scan. There are five scans that you should use to examine your compliance needs. These are:
- Active internal and external scans
- Mimics an actual attack so you can identify your weaknesses.
- Passive internal and external scans
- Examines your current configuration to define your level of security.
- Personal identifiable information
- Discovers the Character User Interface (CUI) and uses scanning data to determine what to do about it.
- Dark web scan
- Uses software to examine if any data has been stolen and determines how to stop a hacker in their tracks.
- Phishing simulation
- Analyzes where your staff stands with their level of compliance comprehension and pinpoints training; they may need to identify/stop a future attack.
After the scans have been completed, it is time to build and examine your data workflow. This is where you inspect current employees, third party vendors and other personnel to discover how sensitive data is being communicated and handled to see if there may be room for a hacker to access the information. This is also a time to find out whether your vendors meet compliance; if they do not, you will not be awarded a contract moving forward.
Now that your assessment is complete, what are the next steps?
After completing your risk assessment, it is time to prepare an executive summary. This summary outlines your organization’s gaps, risks and recommendations for moving forward. This leads you to examine your System Security Plan (SSP), which evaluates every single control, how you are remediating these controls, and the documentation of your security plan. If this plan is done correctly, then you can begin the auditing process.
Pro tip: The better the documentation is in your SSP, the faster you can fly through the audit process and receive your compliance certification. This is where many contractors fall short and mistakenly let information slip through the cracks.
Next, you should review your Plan of Action and Milestones (POAM). This is where you review your controls to find what may be missing and putting a plan in place. This is part of NIST 800-171 and may buy you time when submitting a contract while waiting on your compliance.
Once you complete your POAM, you will use your Discovery Report to verify the evidence that your controls are in place.
With this stack of security measures, what is the price behind the service?
We’ll be honest! Your solutions do not need to be overly expensive. We make affordable recommendations for your organization to gain compliance.
The key is to start where you left off. Most organizations find themselves at the third level of CMMC compliance, which is explained in the outline below:
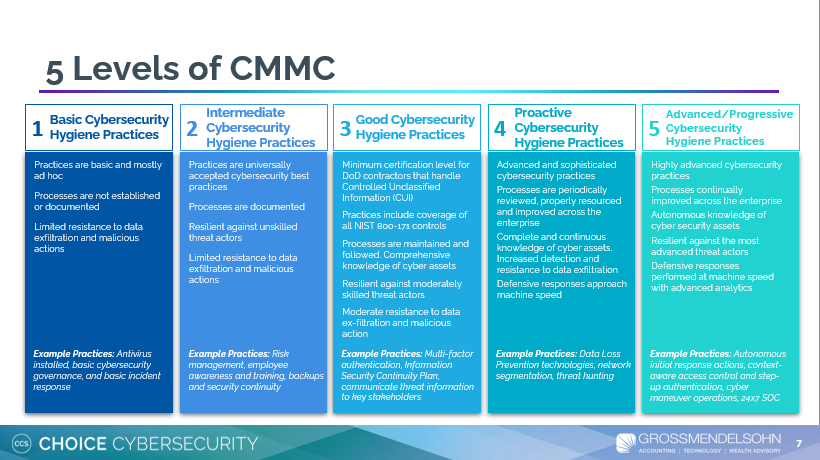
Once your documentation is in order and you have identified what level of compliance you have, you can then bring in your team of cyber security experts to assist you in getting your certification across the finish line.
An important note is that there will be numerous components needed to become compliant. It is better to have a team of experts with different skill sets (administrative, physical, technical, etc.) to help you obtain your certification. Think of it as a total package solution to compliance!
Here's a recap of the process:
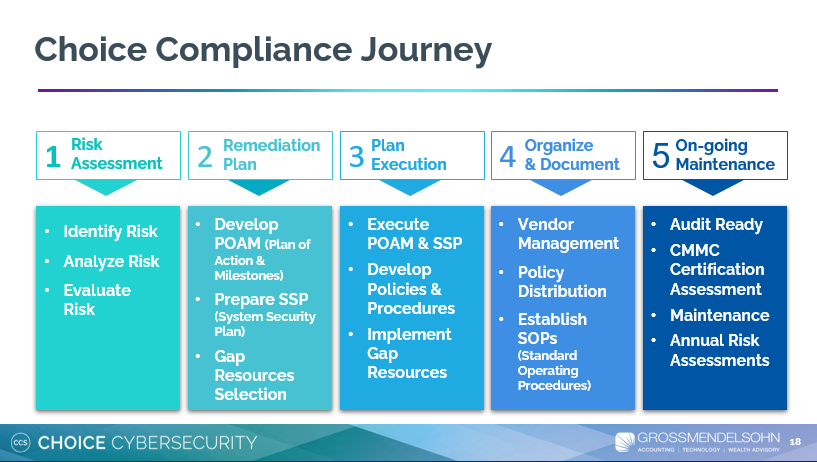
The end goal, plus some good news!
As a contractor your goal should be to jump into this process sooner rather than later. The DoD wants every contractor and subcontractor certified by 2025.
The good news is that your organization can receive a 50% tax credit on your cyber security services if:
- Your business is a Maryland based corporation
- You are paying Maryland state taxes
- You have 50 or less employees
You can learn more here.
Questions?
If you have questions on whether you meet the qualifications for a tax credit, or would like to learn more about our services and how we can help you obtain your certification, contact us here or call 800.899.4623.


.png?width=500&height=500&name=Cyber%20Security%20Wake-Up%20Call%20Screen%20Play%20(1).png)