What do you do when you find someone doing something illegal on the internet? There’s no superhero seeking out cyber criminals on your behalf and sending them off to the police department. You can call the police if you’ve experienced a substantial cyber crime like a major ransomware hack or identity theft. However, the run-of-the-mill cyber criminal can steal from you and get away with it for a long time before ever getting caught.
You might be surprised to know that there are several effective online tools to report a cyber criminal. Let’s look at some common cyber crimes, how to spot them and what to do about them.
Devilish Domain Cybersquatters: How to Spot Them
You might not know this, but someone could be replicating your domain and stealing your website traffic and online reputation.
The legal term for this is “domain cybersquatting and the bad faith intent to profit (Revision Legal).” It’s a form of copyright infringement where a user makes up a fake domain URL that looks like a real domain so they can trick website visitors and collect information.
We’ve seen it with our clients as well. Just last month, a cybersquatter created an exact replica of our client’s website, but the domain name was slightly off to the point you almost wouldn’t notice it. An example would be G00gle.com (with zeroes instead of letter Os) rather than Google.com. It catches mobile users because you’re less likely to notice the differences on a mobile interface.
Cybersquatters will also purchase alternate domains like .net or .org. Small companies may not think about purchasing their .com domain along with a few others like .net or .biz, but these additional domains are just more options for sale on the internet.
How Do You Kick Out a Domain Cybersquatter?
 Once you’ve found the fraudulent freeloader, what do you do?
Once you’ve found the fraudulent freeloader, what do you do?
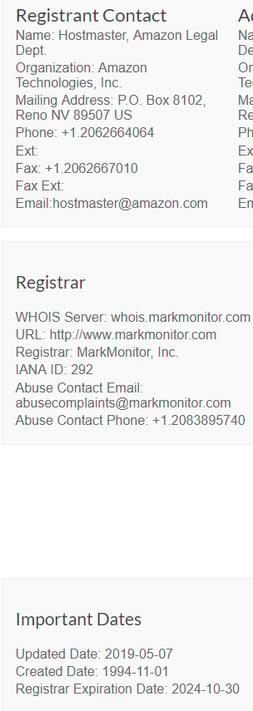
First, find out who the domain registrar is. A great tool for this is the whois lookup from ICANN, which allows you to enter a domain to discover who owns it. Let’s see it in action.
The image to the right shows the ICANN report from amazon.com. ICANN will tell you who the domain’s contacts are and who the registrar behind the domain is. It will show you when the domain was created and, most importantly, will have an abuse contact phone or email.
Once you know who the domain registrar is, contact the abuse email and provide the following information:
- The nature of the suspected abuse
- How the activity has impacted your business
- What terms and conditions the cybersquatter violated
While you can’t always find the registrar’s terms and conditions, including all three of these pieces of information will help the moderator take you seriously and shut down the affected domain.
Here’s another scenario: What do you do if the domain registrar does not respond? Are they in cahoots with the cyber-criminal?
Probably not, but depending on the company, you may need to allow them two to three business days to process your request and evaluate your claim. If you are certain your request is going unchecked, you can take it to the next level and report the initial removal request along with a complaint about a lack of response from the domain registrar here.
Caution: This is a last resort option. Make every attempt to reach out to the registrar through the phone and email before making this step.
Recognizing and Reporting Evil Email Spoofers
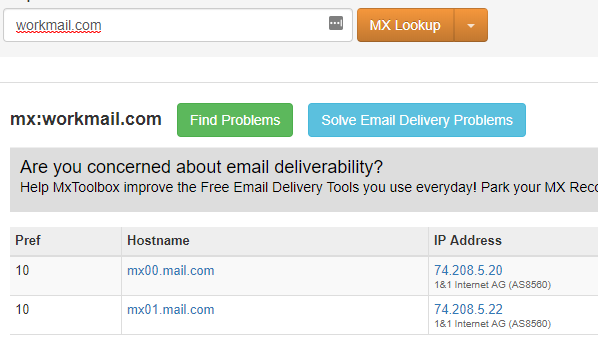
Cyber-criminals aren’t just creating websites and domains with malicious intent. They can also create an email that mimics real people. However, the people you contact for this may not be the same people you contact for the domain. In this case, you may need to contact both the domain registrar and the email service provider. Find out who the email service provider is by using this tool.
Here’s a quick case study: Jenny at ABC Manufacturers got an email from the controller, Dennis, asking for copies of W-2s. When she looked at the email address closely, it was dennis@workmail.com rather than dennis@abcmanufacturers.com. Using MXToolbox, our tech team researched workmail.com and found that it was owned by mail.com. Then, we visited mail.com to find their abuse policy and contacted them through their website to report a policy violation. In less than one hour after submitting our request, mail.com responded that they would suspend the account immediately.
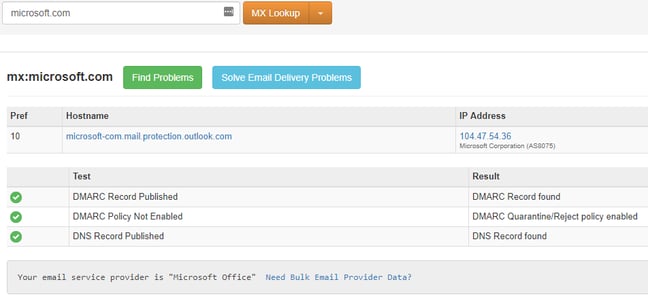
MXToolbox is very clear with telling you exactly who the provider is in layman’s terms, rather than complex IT terms. In the image below, you’ll see that the MX record is rather long and confusing, but down at the bottom it clearly says “Your email service provider is Microsoft Office.”
Dealing With Yahoo/Gmail Bandits
Email spoofers don’t always find an updated email account to replicate your address. They’ll create a free Yahoo or Gmail account with your name so it looks like it’s coming from you.
In this case, you already know who the provider is, so you do not have to contact MXToolbox. All you need to do is find the abuse policy and report it.
To report Gmail abuse, go to this webpage.
To report Yahoo mail abuse, go to this webpage.
You can usually find the abuse policy by searching “Yahoo Email Abuse,” but on rare occasions you’ll have to do some digging before finding the right webpage. Again, in any case be sure to gather up the terms from the provider along with any and all correspondence that proves their user is trying to mimic you and cause harm.
Once you’ve done all these steps, you can report the criminal activity to the IC3, which is a branch of the FBI that investigates internet crimes. Most reports get logged into a database, but they can step in for major crimes. Here’s where you can report the cyber-crime.
Why Are You Being Targeted by Cyber-Criminals?
It’s easy to believe the cyber-criminals have a virus on your machine, watching your every move and learning how they can properly mimic you. While this is possible, it’s usually not the case.
The vast majority of the information cyber-criminals obtain is searchable on Google. They look at Facebook, LinkedIn, and your company’s website to learn about you. The more you post about yourself online, the more ammunition they have to imitate you. Be very cautious of what you post online as it can be accessed by the bad guys.
Need Help?
If you are facing spoofing, cybersquatting or black list issues, you should check with your IT provider so they can do a deep dive to pinpoint the problem. Contact us here or call us at 410.685.5512 for help.


