With the number of cyber threats targeting your business, cyber security should always be top of mind. With hackers changing their methods so frequently, how can you keep up?
Even though cyberattacks are getting more sophisticated, there are a few shockingly effortless ways to keep up on cyber security. In fact, even your grandma can handle these cyber security tactics.
1. Click “Yes” When You’re Prompted to Update
You know those annoying pop ups that say “an update is available for you”? (Pro tip: do not click “ignore for 30 days.”) It turns out those updates are really important, and putting them off only puts you and your business at risk.
As new cyber threats emerge, software vendors like Microsoft and Sage will release updates designed to protect users. Keep in mind that not everything is covered through Windows updates for your PCs and servers. Your workstation will release specific updates such as BIOS, chipset driver/firmware, hard disk controller, graphics driver updates and more. Your PC vendor (Dell, HP, Lenovo, etc.) will simply push a notification to your desktop to alert you of these updates. All you have to do is click “yes” and the update will begin.
We strongly recommend that you do routine maintenance on your servers and network once a month. This includes installing important updates. Without these updates, you’re leaving your servers and workstations vulnerable to an incoming cyber threat.
You may be tempted to click on those pesky internet pop up ads that say “Your computer is in danger: download this software now” in an effort to keep your computer updated. However, it’s critical that you first verify that the update is coming from a legitimate source. Otherwise, you might end up downloading a nasty virus that even your grandma’s trademark TLC can’t fix.
2. Install Reputable Antivirus Software
We all know that antivirus software is not the end-all be-all solution to safeguarding your network from a threat. However, that doesn’t mean you should throw in the towel on antivirus software altogether.
Creating a secure environment requires piecing together several layers of protection. While it’s not 100% secure, effective antivirus software is one of those layers of protection you still need.
Antivirus software will protect your business from internet threats, but we shouldn’t forget about advanced spam filtering. Advanced spam filtering services, such as AppRiver Secure Tide or Microsoft’s Advanced Threat Protection, catch glaringly-obvious phishing emails, emails with malicious attachments or links, and more.
As your grandma will tell you, you can’t expect to grow big and strong without eating your vegetables. Well, antivirus software and spam filtering services will help grow an impenetrable cyber security protection plan.
3. Think Before You Click On That Email
Your grandma may have fallen prey to that free pizza email scam, but with these tips, we hope you’ll be wise enough not to.
The majority of threats today are delivered to your inbox and it only takes one click for them to wiggle into your system. Here are a few trademark ways you can identify an untrustworthy email:
- The email has an attachment
- There’s a link in the email
- Your coworker or boss is asking you to purchase gift cards
- You’re being asked to share confidential or financial information
- Words are misspelled and poorly phrased
- There’s a sense of urgency to a specific task requested in the email
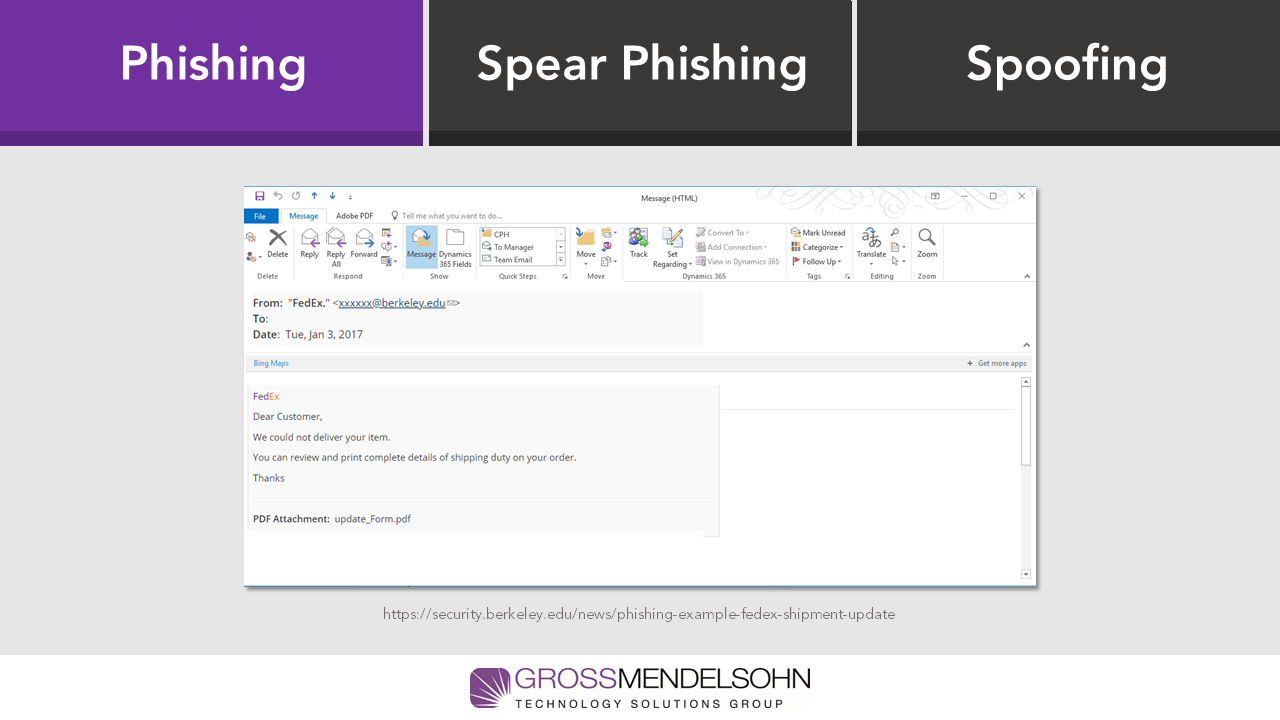
Let’s see if you can identify the red flags in this example from our cyber security guide:
See if you spotted them all by downloading our cyber security guide.
Some of these items we expect to see in an email. We send internal emails with attachments all the time. We also constantly receive mass emails with specific links to click. The key is to think about the sender and ask yourself…
- Was I expecting an attachment (like an invoice) from this person?
- Does the language in the email sound like it actually came from them?
- Is there poor grammar or spelling?
Just because an email looks like it came from someone you know, doesn’t mean it did. It could have been spoofed and bring you nothing but problems. This is where those advanced spam email scanning solutions help weed out threats before they even reach your inbox.
Remember that the #1 way to prevent a cyberattack is with thorough and frequent cyber security awareness training. If you or your staff are out of touch with the latest cyber security best practices, you can download and share this guide for free.
4. Set a Reminder to Change Your Password (and Set a Good One)
We know grandma’s password is the name of her precious cat (we know you’re not judging). However, it’s time for you and your grandma to get your passwords up to date with current standards.
New password standards dictate that phrases are more secure than words and symbols, so you can suggest to grandma that a password like IL0veMyGrandchildMoreThanMyCat! is way more secure than MrFluffy1942.
While it’s no longer recommended that you switch passwords all the time, you can set a reminder to update your password every year or so to keep those hackers on their toes. However, if a app or website you use gets hacked, you should change your password immediately, as it has likely been compromised.
You should vary your passcodes from account to account as well. It sounds like a pain, but just think: if just one of your accounts is compromised, then the hacker has access to all of your accounts that use that same passcode. Scary, right?
There is help out there for those who can’t remember what they had for breakfast that morning, let alone 30 unique passwords. Applications like LastPass, Dash Lane, Keeper and TrueKey help keep your passwords safe and secure. Plus, these apps will generate secure passwords for you and remember them on the sites.
5. Set Up Two-Factor Authentication
If you’re reading this with your grandma, here’s the skinny on two-factor authentication: two-factor authentication is a second force to pass through in order to access vital information. For instance, many iPhone users are able to download apps by simply writing in a password or using touch ID. However, in order to access iCloud from your desktop, which holds a wealth of your personal information, you have to log in using your password on the desktop app, and confirm the code that is texted to your iPhone in order to access the files.
Go ahead. We’ll pause here so explain to your grandma what the Cloud is.
By enabling two-factor authentication, you can catch invalid login attempts immediately. Imagine this: you’re sitting at your desk and your phone gives you a notification from Office 365, asking you to approve your login attempt. Your first thought is, WHAT LOGIN ATTEMPT!? In this case, a malware hacker may have your email credentials and is trying to infiltrate your Office 365 account to monitor and send emails as you. Thanks to two-factor authentication, you’ll know that hacker’s every move and stop them in their tracks. Now, you’ll only spend 10 minutes updating your Office 365 password and briefing your IT group, rather than three days dealing with a post-hack situation, connecting with clients the hacker reached out to on your behalf, and sleuthing out how many files were compromised.
6. Keep Your Backups Updated
This one might be a stretch for you to do yourself, but if nothing else you can remind your IT person to stay vigilant on keeping your backups up to date.
Having an automatic backup in place is critical. In the event that a phishing threat passed through undetected and a ransomware threat took hold of your network, you need an up-to-date backup to restore all those files and get your network back up and running. You’ll also need to frequently test backups to ensure everything is working as expected.
Need Help?
There’s not one simple solution to cyber security, but with these easy tips, both you and your grandma will fend off the major cyber threats knocking at your door. Contact us here if you have questions.